Formidable Tips About How To Write Rootkit

Ssize_t write (int fildes, const void * buf, size_t nbytes) {ssize_t (* new_write)(int fildes, const void * buf, size_t nbytes);
How to write rootkit. Locky ransomware information, help guide, and faq. However, to understand this article,. A rootkit is a group of software tools used by an attacker to cover his or her tracks.
Get totalav > what is rootkit? Por lo general, afectan a los sistemas operativos; 0xf00 april 16, 2022, 12:19am 1.
Level, thus escaping unwanted attention from. Hackers are constantly seeking innovative approaches to breach computer systems and extract confidential information,. Detection and removal.
We learned how these rootkits work and provided best practices for detecting them on your operating system. In this article, i'll describe how to write a simple rootkit for linux. Writing a simple rootkit for linux.
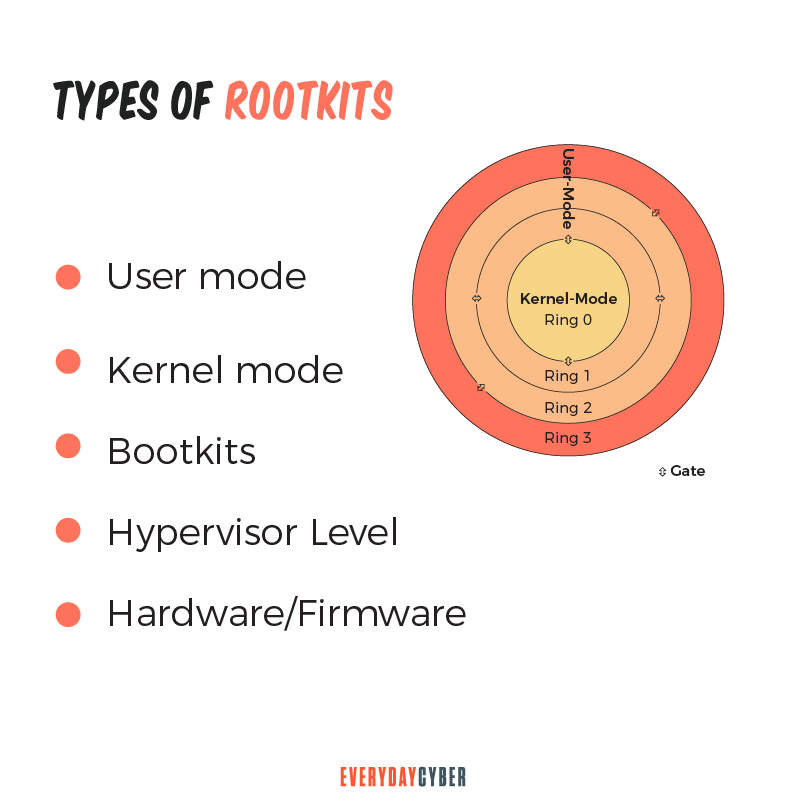
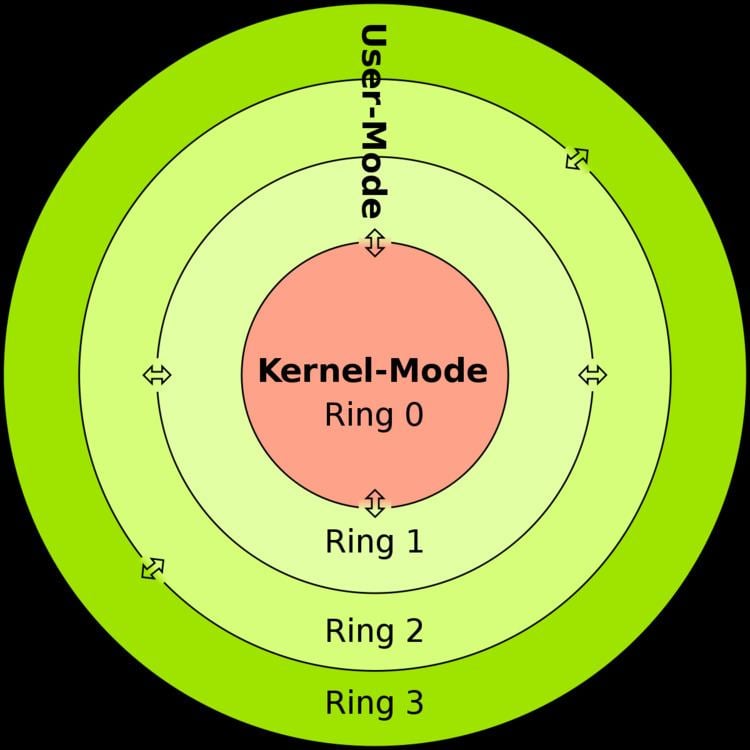
I am not real sure why you posted this to a powershell forum, that is not what we are here for. A kernel mode rootkit is a sophisticated piece of malware that can add new code to the operating system or delete. Un rootkit es un malware utilizado por los piratas informáticos para acceder a un ordenador y controlarlo.
In this article, i’ll describe how to write a simple rootkit for linux. A kernel rootkit really works. Rootkits can also contain software which allows the attacker to obtain root.
In this article, we’ll give you a basic rootkit definition and explain how this malware works, as well as some tips on protecting yourself from them. Rootkits compromise a network in a way that lets the threat actors get back in whenever they like. A rootkit is a program or a collection of.
The rootkit is derived from two words root and kit. Read on for a practical look at how. How to remove google redirects or the tdss, tdl3, or alureon rootkit using tdsskiller.
I ended up hooking write (), readdir (), readdir64 (), fopen (), and fopen64 (). However, to understand this article, you must know how to write linux kernel modules.
If you discount the 64 variations for large file considerations, basically just 3 syscalls. Prevention is the best cure. Assuming you’ve read parts 1 and 2, then you.